
2 Understanding the Genesis Preferences
2.5 Database
This section describes the more "advanced" areas of Genesis. Most Internet dialup users (ie. those simply using Genesis to connect to their Internet Service Provider) will barely need to worry about this section.
The databases are uses to add programs that require Genesis, add/remove access from remote users, setup servers on your network etc.
2.51 Groups
The db/group is the group database for the AmiTCP/IP system.
Each line in this file defines a group. Groups are really only required for
external programs such as NFS.

db/passwd.
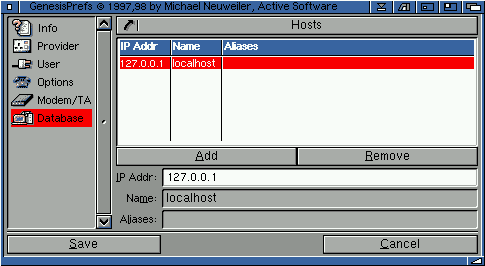
2.52 Hosts
The hosts sections contains the host name to IP address mapping table. The host names cannot be used by the TCP/IP protocols directly, but they must be mapped to IP addresses before they can be used.
2.53 Protocols
The protocols section contains the protocol name to protocol number mapping table. This allows users to refer to protocols using symbolic names instead of numbers.
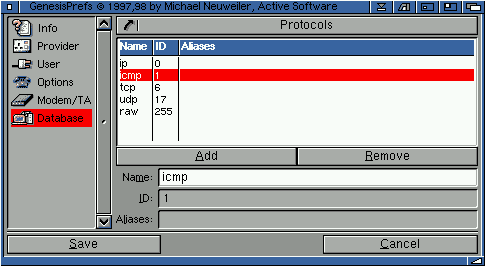
The official protocol names and numbers are described in the "Assigned Numbers" RFC. For example,
tcp 6 TCP transmission control protocol
2.54 Services
The services section contains the service and protocol name to port number mapping table. This allows users to refer to services using symbolic names instead of port numbers.
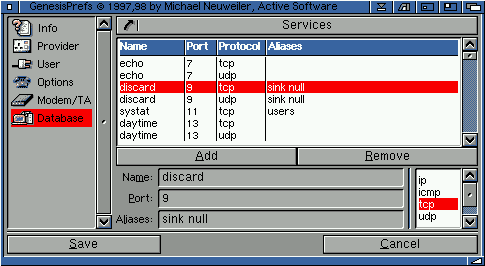
The services for port numbers 0 through 255 are assigned in the "Assigned Numbers" RFC.
For example,
shell 514 tcp remote login service
2.55 Access
Genesis implements an access control feature similar to `tcpd' inside the protocol stack. This means connection doesn't even get established if the connection is to be denied, remote end just gets the usual `connection refused' error message.

When connection request arrives, the access entry list is searched through sequentially line by line until a match is found. Access entry lines looks like the following...
[service] [host/mask] [access] [log]
It is first checked whether the port where connection is made matches the
port given
Now, if port matched the source host internet address is compared with the host value given in current access entry. Mask can be used to ignore some bits when comparing, for example whole subnet can be checked with only one entry in access control list. The host value may also contain that mask information by having `*' in place of some number in host value given in internet not notation format (see the examples).
A special hostname `$' matches to all hosts, except it does not allow source routing. Source routing is disallowed also if connection matches to an entry with a specified host.
If host matched, The next thing to do is to see whether connection is to
be accepted or not. if
If LOG is written last in the access entry list, Info whether connection was accepted or denied, with corresponding remote host and destination port is written to the syslog.
| Service | Host[/Mask] | Access | Log |
|---|---|---|---|
| finger | 127.1 | allow | LOG |
| * | 130.233.*.* | allow | |
| nntp | 130.233.0/255.252.0.0 | allow | LOG |
| $ | *.*.*.* | deny | LOG |
| * | $ | allow | LOG |
The list tells that finger queries from local host is to be logged. (2) All connections from hosts whose addresses start with 130.233 are to be allowed and (3) hosts in a bit wider set of class b -networks can access nntpd server of this host. and these connections will be logged. Next line tells that connections to any incoming server ports are to be disallowed and the last one will then allow the rest ports without source routing and this activity will be logged. Without this line these connections would be accepted silently, since that would be the default operation if no matches were found.
The last 2 lines in that example are quite useful. It does permit ftp to work since it binds a data transfer socket greater than 1023, but it disallows unwanted hosts to access normal features effectively. Also nonstandard services, such as netfs and irc are access controlled in this access control list.
2.56 Inetd
Inetd is the configuration section used by the built in inetd. Entries within this file can consist of many lines. Inetd must consist of one entry for each server to be able to start. Each entry has following format:
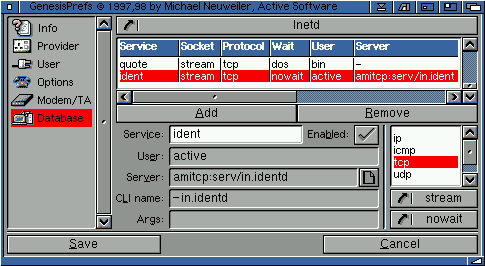
Genesis re-reads an updated inetd database when new services are added, deleted or modified.
Inetd examples:
telnet stream tcp dos bin - echo The telnet service is not installed
ftp stream tcp nowait root AmiTCP:serv/ftpd ftpd -l -x
The first entry would respond to telnet service (which is only available for TCP, which is the only stream protocol) by launching the DOS program echo with arguments "The telnet service is not installed". This causes the string "The telnet service is not installed" to be printed on the telnet client console, if anyone would try to telnet to your machine.
The second entry is the entry for the FTP server provided with Genesis.
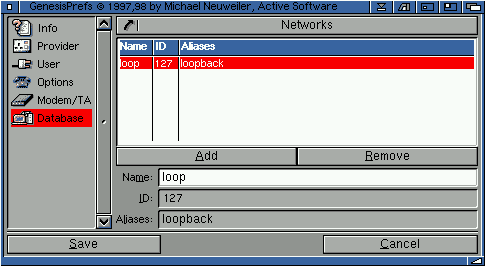
2.57 Networks
The networks database contains the network name to IP network number mapping table. The network names and the corresponding IP network numbers are rarely used, so this file normally contains only the entry for the `loopback' network (whose official network number is 127).
Go to the previous, next, chapter, table of contents.